During the past week Gauss Security R&D department discovered a new evasive malware that is linked to Charming Kitten (APT35).
Upon execution the HYPERKITTEN sample, it checks if the computer belongs to Israel and then drops a second undetected payload. The second payload copies an encrypted shellcode:
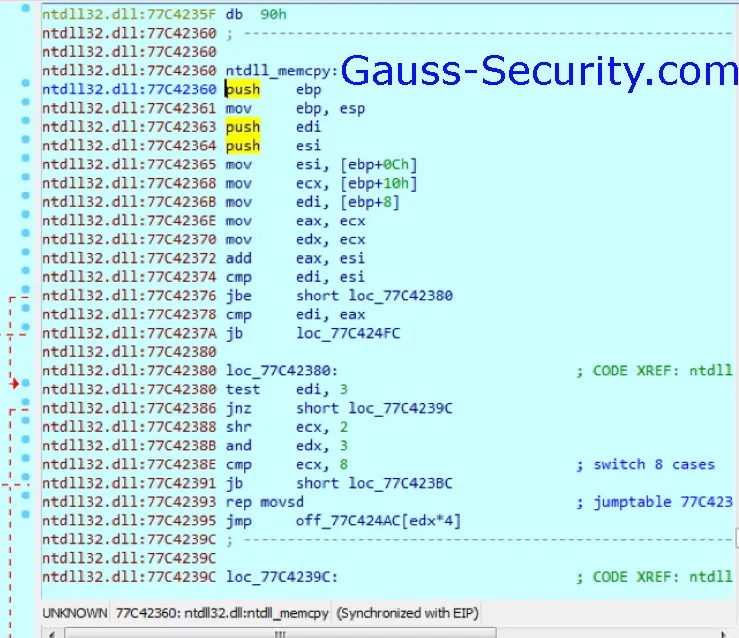
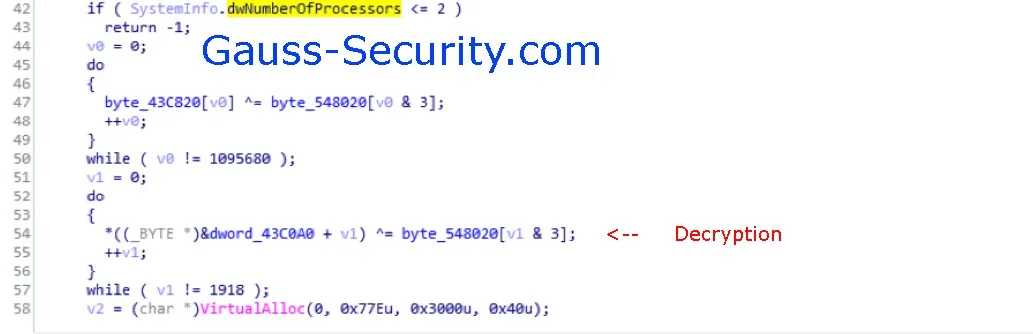
Only if the number of cores is ≥3, HYPERKITTEN continue in the preparation of the third stage and attempts to decrypt the shellcode. The shellcode attempts to elevate privileges and will try to connect to one website among a list of dummy websites.
Gauss Security found that one of the websites was also used by CharmingKitten as a command and control server in previous cyber attacks.
The shellcode also have the ability to download and execute additional malware, key-logging and allowing it’s operators to take full remote control over the infected computer.
Gauss Security R&D department have performed detailed analysis and have provided Mitigation Strategies for it’s customers.
As always, we ensure that our customers will always stay protected and secure against the latest threats.
We are currently observing their techniques and will provide more information about HYPERKITTEN, when it will be possible.
In case you found anything related to CharmingKitten contact us via our website.
