CVE-2024-41818 was discovered by our R&D team
The ReDOS vulnerabity was discovered in fast-xml-parser npm package
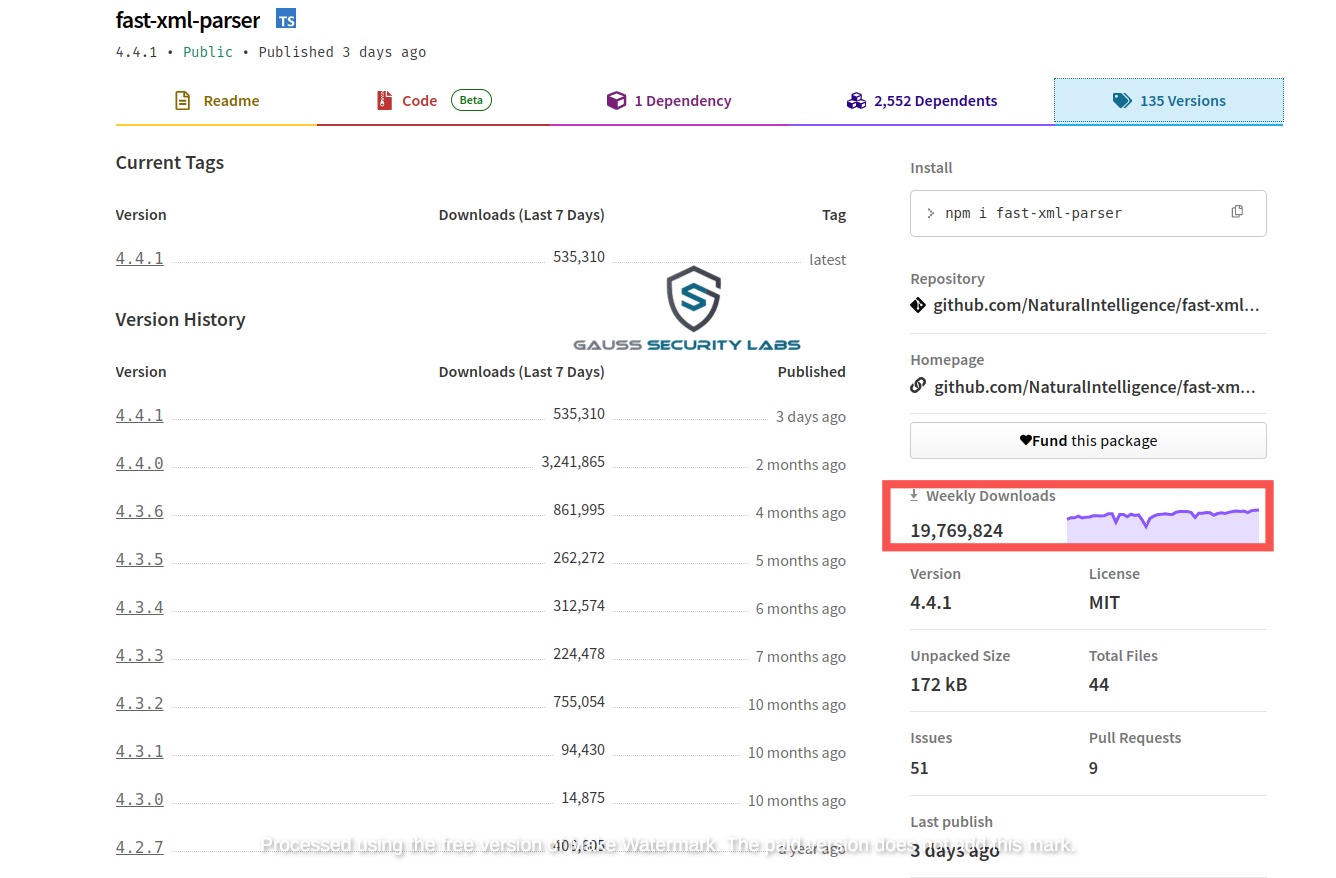
fast-xml-parser is a very popular npm package that has more than 19 million weekly downloads
It is used to Validate XML, Parse XML to JS Object, or Build XML from JS Object without C/C++ based libraries and no callback.
Vulnerability Analysis
A vulnerable Regex exists at line 17 on the file currency.js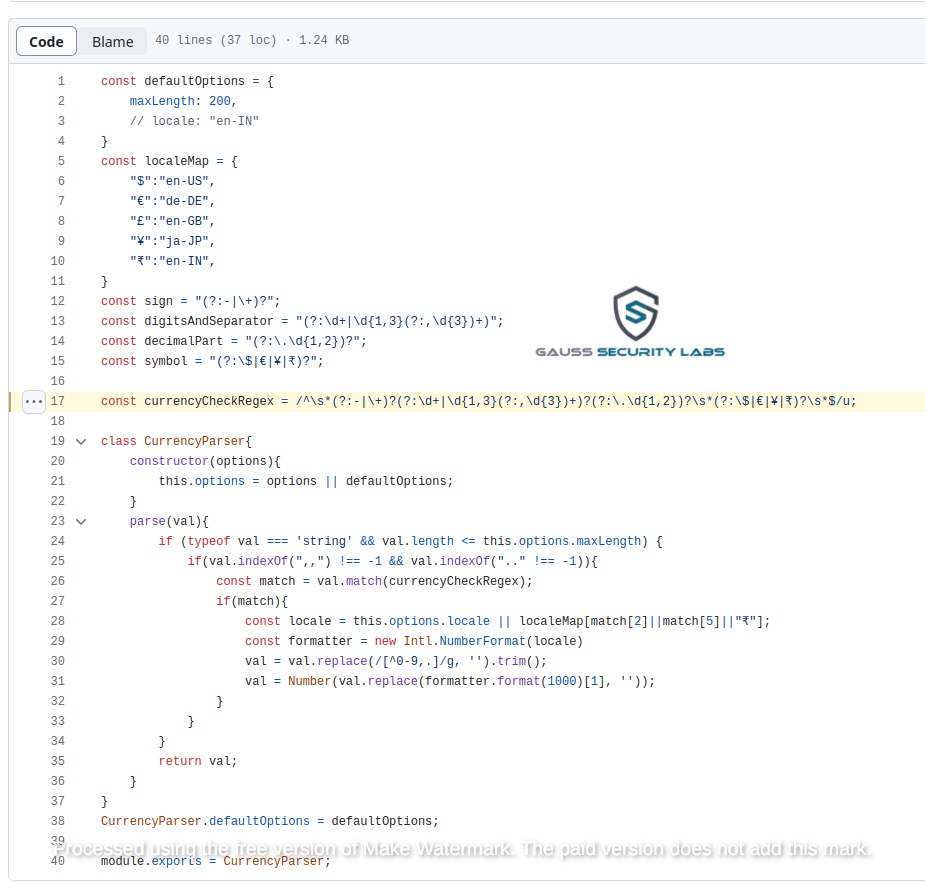
The vulnerable currency regex is used as part of CurrencyParser.parse method
An attacker can provide a specially crafted string to cause DoS and crash the Node.JS application.
Since Node.JS is a single threaded application, An attacker can easily consume all web server resources and cause DoS
Analysis Of The Security Fix
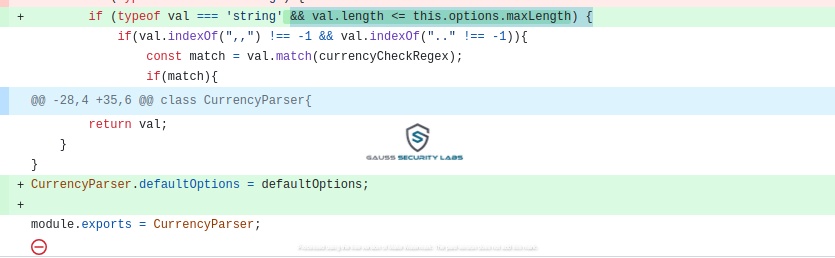
We can see that the developer added a length check for the input string
By restricting the maximum string length to 200 the vulnerability is properly mitigated
Mitigation
To fix the vulnerability make sure to upgrade fast-xml-parser to version 4.4.1
Securing Third-Party Software: Safeguarding with AppGuard
Ensuring the safety of your third-party software libraries is crucial in defending against latest security vulnerabilites.
Our solution is called AppGuard, which was developed by our Elite R&D team
(35 Elite cyber security professionals, including former members of the IDF 8200 unit)
AppGuard provides robust security measures to verify and monitor these libraries, ensuring they are free from vulnerabilities and malicious code. This proactive approach helps maintain the integrity of your software environment and protects against potential threats.
For more information on AppGuard capabilities and how to stay protected, contact us here.

References
https://github.com/NaturalIntelligence/fast-xml-parser/security/advisories/GHSA-mpg4-rc92-vx8v
